Despite the benefits, complex projects such as a migration usually carry significant risk, which may inhibit those plans for progression. To help you mitigate risk, we have compiled four tips from our industry thought leaders to ensure your DCS upgrade or migration project moves forward without compromising safety or compliance.
Blog
Industrial Modernization Doesn’t Have to Be Hard
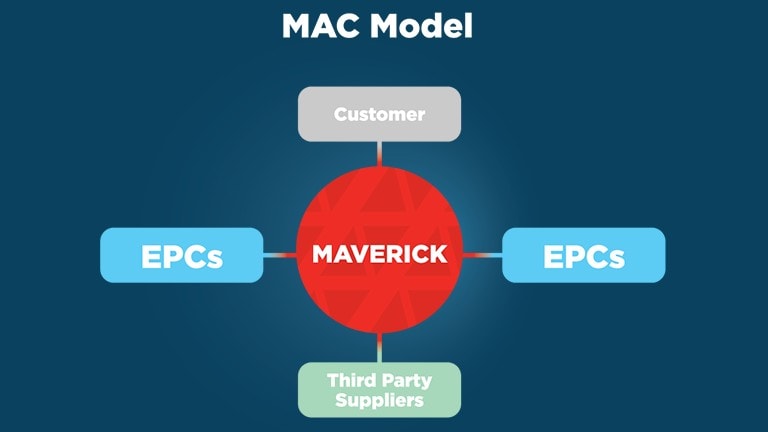
Lead Your Facility into the Modern World with a Main Automation Contractor The industrial world as we know it is changing – fast. Legacy system obsolescence, cybersecurity […]
How to Do State-Based Control Well
In previous blogs in this series, we discussed what state-based control is and how it works; its advantages and disadvantages; and how it all fits in the […]
How Much Are You Paying For Your Legacy DCS?
Your old DCS could be costing more to maintain than to replace. It’s a shocking thought, but it’s often true when all costs are considered.